If you’re hosting your WordPress site on a Synology NAS using Docker, and you want to audit users or verify critical settings (e.g., to check for signs of unauthorized access), this guide walks through the secure steps to connect via SSH and access the MariaDB database.
⚠️ Sensitive values such as IP address, usernames, passwords, and database names are omitted for security reasons. Replace placeholders (
<...>) with your actual settings.
✅ Step-by-Step Guide
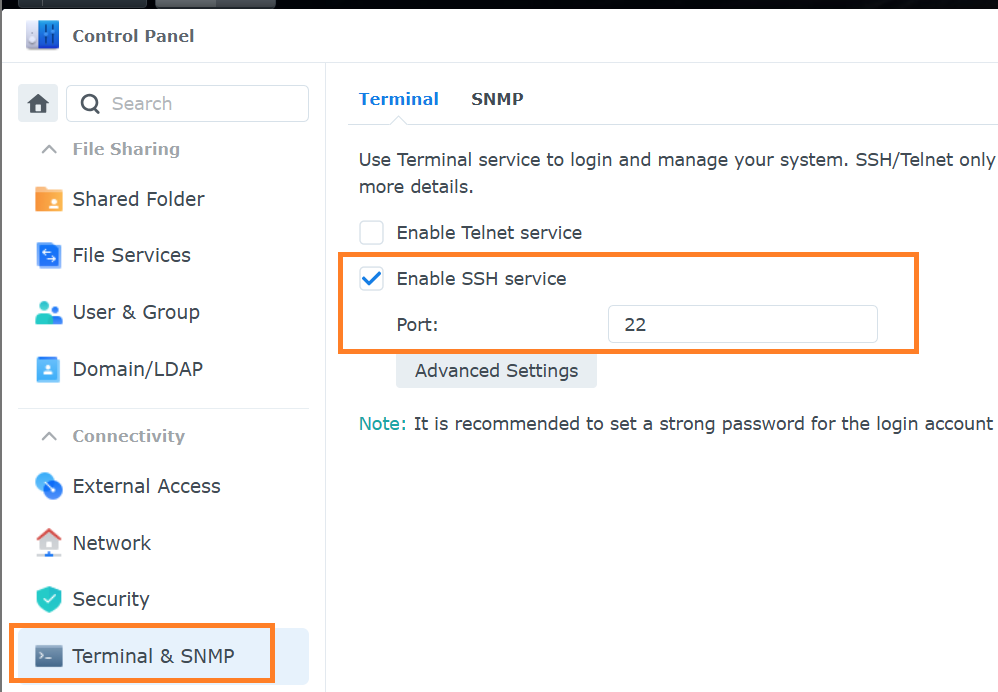
1. Enable SSH on Synology NAS
- Log into your Synology DSM interface.
- Go to: Control Panel → Terminal & SNMP → Terminal.
- Check ✅ Enable SSH service (typically on port 22).
- Apply the changes.
2. Connect to NAS via SSH from Windows
Open a terminal (Command Prompt or PowerShell) and run:
ssh <your_nas_username>@<nas_local_ip_address>- Enter your NAS account password when prompted.
- You are now logged into the NAS system via SSH.
3. Check Running Docker Containers
To see the active containers:
sudo docker psLook for a container running MariaDB — typically named something like mariadb-wordpress.
4. Access the WordPress MariaDB Container
Run this command to enter the MariaDB CLI:
sudo docker exec -it <mariadb_container_name> mysql -u <db_user> -p- You’ll be prompted to enter the MariaDB user password.
- After successful login, you’ll see something like:
MariaDB [(none)]>
5. Switch to WordPress Database
Once inside MariaDB, switch to the correct database:
USE <wordpress_database_name>;Usually, this is named something like wordpress, wp_db, or similar depending on your Docker docker-compose.yml setup.
🧪 Inspect WordPress Users
Run this SQL query to see all registered WordPress users:
SELECT ID, user_login, user_email, user_registered FROM wp_users;This will return a table like:
+----+-------------+----------------------+---------------------+
| ID | user_login | user_email | user_registered |
+----+-------------+----------------------+---------------------+
| 1 | admin_user | your_email@example.com | 2023-01-01 12:00:00 |
+----+-------------+----------------------+---------------------+
If you only see yourself and no suspicious users, you’re in good shape.
🔍 Verify WordPress Site URL Settings
It’s a good idea to confirm your siteurl and home options are not altered (which can sometimes be used for phishing redirects):
SELECT option_name, option_value FROM wp_options
WHERE option_name IN ('siteurl', 'home');
You should see your actual domain or internal IP in the result, such as:
+------------+-----------------------------------+
| option_name | option_value |
+------------+-----------------------------------+
| siteurl | http://yourdomain.local |
| home | http://yourdomain.local |
+------------+-----------------------------------+
🏁 Done — Exit Cleanly
After checking the data, type exit to leave MariaDB, then type exit again to leave the SSH session.
🔐 Extra Tips
- Never expose your NAS SSH or MariaDB to the open internet.
- Disable SSH when you’re done (optional, for extra safety).


